Why identity-centric addresses may close the compliance gap that keeps enterprises wary of public blockchains
When a chief financial officer resigns, a Fortune 500 company typically scrambles to re-issue signing authorities across dozens of bank portals and smart-contract wallets. Yet the same firm can mint a new token in seconds. The asymmetry highlights a nagging truth: most blockchains were built for open participation, not Sarbanes-Oxley segregation of duties. According to Accumulate, that missing control layer keeps treasurers and auditors on the sidelines.
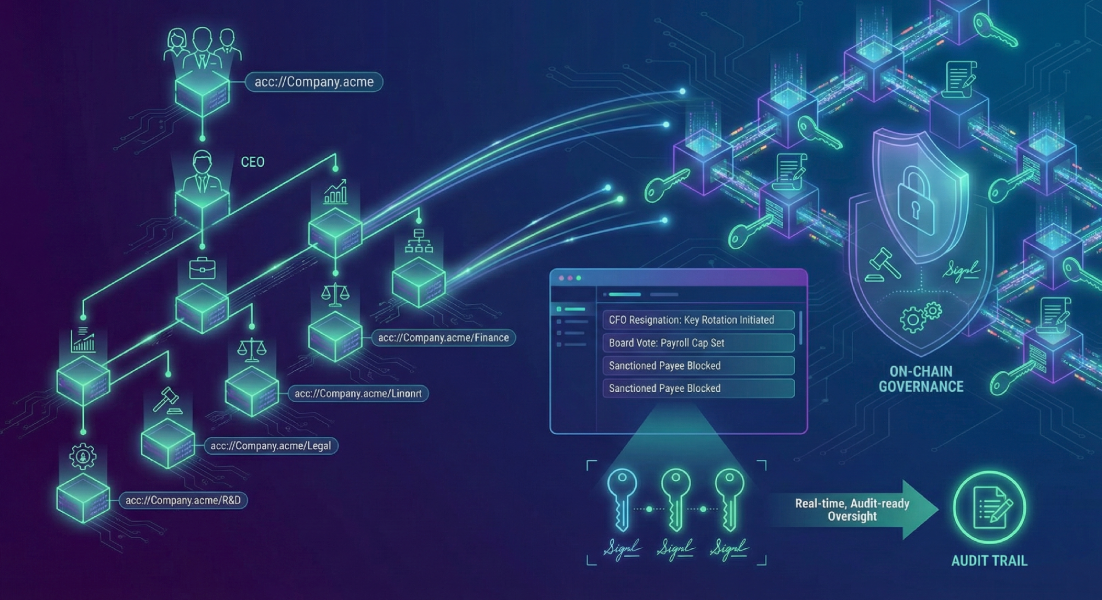
Accumulate’s answer is the Digital Identifier, or ADI—a human-readable address that bundles its own sub-chains for keys, data and assets. Each ADI acts like a mini-blockchain whose rules are defined at creation and enforced by consensus. If the model scales, a board vote could cap payroll, rotate keys or block sanctioned payees without touching a line of Solidity.
The Governance Gap
Bitcoin and Ethereum prioritize censorship resistance, leaving enterprise controls to application-layer multisig contracts. Those contracts improve security but break whenever a signer changes or an opcode is deprecated. External spreadsheets and manual approvals fill the gaps, adding cost and legal ambiguity.
Pilot projects underscore the tension. A DeFi trading desk can settle trades in minutes, yet its treasury still signs withdrawals by hand because the contract cannot enforce tiered limits. That mismatch slows finance teams and dilutes the audit trail. As the 2025 draft U.S. GENIUS Act pushes stablecoins toward bank-grade oversight, the lack of native governance looks less like a quirk and more like a blocker.
Inside an ADI
An ADI resembles a URL— for example, acc://Company.acme—but behind the text lives a bundle of chains that track keys, data and tokens. A Key Book defines who can sign; Key Pages rotate individual keys without redeploying code. Because each chain is native, fees stay flat instead of spiking with gas markets.
Managed Transactions give those chains teeth. Before a signature reaches the mempool, a Manager Key Book can throttle frequency, cap amounts or filter counterparties. The mechanism, first outlined in the 2022 whitepaper, acts like an ATM withdrawal limit written into consensus.
“Managed transactions may enforce a spending limit similar to withdrawal limits on ATMs and allow only a certain number of transactions per day.”
Turning an Org Chart Into URLs
Start with the root identity. The board of Acme Corp creates acc://Company.acme and links a 4-of-7 Key Book. Under that root, each department becomes a sub-ADI—Finance, Legal, R&D—each with its own signers and spending caps. The hierarchy mirrors corporate law: a parent can rotate keys in any child without redeploying contracts.
Suppose Finance holds acc://Company.acme/Finance. A Manager Key Book enforces a 500 k USDC weekly cap and requires two-of-three controller signatures. Legal, at acc://Company.acme/Legal, wields veto power over outbound transfers that match a sanctions keyword. Because every rule rides inside the address, replacing a controller key is a one-line update; the protocol voids the old key at the next block.
Native Beats Contract
Smart-contract multisig wallets on Ethereum have matured, but they remain code objects subject to exploits and version hell. When an opcode is sunsetted, every instance must upgrade or risk funds. By contrast, protocol-native controls treat governance as data, not code. Auditors can diff two block heights and see exactly when a quorum changed—no ABI decoding required.
Cost matters too. Each Accumulate signature occupies a fixed byte length and pays a predictable ACME fee, according to a 2022 blog post on Accumulate Blog. Predictable fees simplify budgeting and reduce the incentive to batch transactions off-chain, a common practice that muddies audit trails.
Beyond the Demo
Managed Transactions extend to equity markets. A 2022 use-case paper on Accumulate Blog describes how an issuer could throttle foreign ownership automatically, maintaining statutory caps without off-chain escrow. Each shareholder class becomes a sub-ADI, and the manager logic rejects trades that breach the ceiling.
CeFi exchanges can apply the same template. Treasury reserves live in a root ADI; each creditor holds a read-only liability sub-ADI. Regulators can compare the two in real time, an idea detailed in a post-FTX article on Accumulate Blog. The design promises proof-of-reserves without trusted intermediaries.
Cross-chain governance is another frontier. Delegated Transactions let an ADI authorize logic on external chains while keeping approval rules at home. In theory, a bank could custody stablecoins on Ethereum yet apply Basel capital limits through an Accumulate manager key.
Operational Considerations
Key custody drives human workflow. Most corporations will pair ADIs with multiparty computation wallets or hardware security modules so no single employee holds a raw private key. Hardware rotation maps neatly to Key Page updates, aligning cryptography with badge-access procedures.
ERP events can trigger on-chain actions. A new hire in Workday could spawn a junior-analyst key limited to office-supply spend. When HR flags a departure, a webhook revokes the key in seconds. The ADI becomes a real-time mirror of the HR database.
Regulators demand audit trails. Because every signature and policy lives on-chain, external auditors gain a single source of truth. The design echoes the “trust but verify” mantra that examiners apply to bank call-report data.
Risks and Mitigations
Key compromise is the obvious nightmare. Emergency pages can freeze spending, but teams must rehearse the process or the control degrades into theater. Quorum loss is subtler; if several directors lose keys, the board could deadlock. Best practice is to store a sealed recovery key with an independent custodian who releases it only after notarized minutes.
Legal recognition varies by jurisdiction. Some regulators now accept on-chain votes, while others still require paper filings. The EU’s MiCAR and the U.S. SEC’s September 2025 stablecoin concept paper illustrate how statutory details diverge. Until case law settles, boards should mirror ADI resolutions with traditional filings.
Protocol risk remains. Accumulate is young relative to Bitcoin, and enterprises will want assurances on validator diversity, code-audit cadence and upgrade paths before locking critical assets to any chain.
The Road Ahead
Stablecoin settlement volumes already eclipse those of major card networks, and regulators are shifting from prohibition to prudential oversight. As institutions map real-world assets on-chain, the question is less whether they will use public ledgers than how they will prove control. Accumulate’s identity-first model offers one blueprint: make the address itself the rulebook, then publish every edit forever.
If that vision holds, corporate governance could move from boardroom PDFs to block-height snapshots. The reward is not just faster payments but a live, unfalsifiable record of fiduciary duty—an audit log too stubborn to ignore and too public to hide.
Sources
- Accumulate. “Accumulate Whitepaper v1.0.” 12 Apr 2022.
- Accumulate Blog. “Delegated Transactions.” 21 Jul 2022.
- Accumulate Blog. “Tokenizing Public Equity Markets.” 13 Oct 2022.
- Accumulate Blog. “Audit Trails for CeFi Creditors Using ADIs.” 22 Nov 2022.
- U.S. SEC. “Stablecoin Regulatory Framework (Draft).” 15 Sep 2025.
- Particula. “From MiCAR to VARA: Mapping Stablecoin Reserve Standards Worldwide.” 10 Oct 2025.












Discussion