Protocol-level governance brings bank-grade controls to digital assets—no oversized wallets required
Stablecoins handled 18.4 trillion dollars of transfers in 2024—more than Visa and Mastercard combined, according to Crypto.com. The money never sleeps: settlements clear every hour, including weekends, forcing treasurers and regulators to re-think controls at internet speed.
The cost of weak controls became notorious when FTX insiders could route customer funds without a second signature, a governance void later detailed in a 2022 enforcement filing by the SEC. For institutions now weighing large on-chain positions, the lesson is blunt: a lone credential—lost, misused or coerced—can vaporize billions.
Traditional finance avoids that single-point failure with segregation of duties: one desk initiates, another approves, auditors verify. Translating the same rigor to blockchains demands more than a bulkier hardware wallet or another password; it calls for governance rules that the ledger itself enforces.
Why the Single-Key Model Breaks Down
Most institutional wallets still depend on one private key—or an MPC-reconstructed shard set—controlling an omnibus address. Anyone who assembles the threshold can empty the vault in one transaction. Auditors at PwC Switzerland warn that key compromise remains the top custody risk precisely because no native mechanism forces a second signer.
Regulators are closing the gap. The SEC’s 2023 Safeguarding Rule proposal emphasizes qualified custodians, surprise examinations and on-chain asset segregation—standards a single-signature wallet cannot satisfy, as the agency’s own release makes clear.
Off-chain fixes such as multi-party computation improve secrecy but relocate policy logic to an application server. If that orchestrator deems a forged transaction valid—by error or breach—the blockchain still records the spend because the cryptographic threshold is met. The root problem is architectural, not cryptographic.
Institutions therefore need controls that live where the risk resides: inside the protocol’s identity layer, untouchable by mis-configured policy engines or hurried contract upgrades.
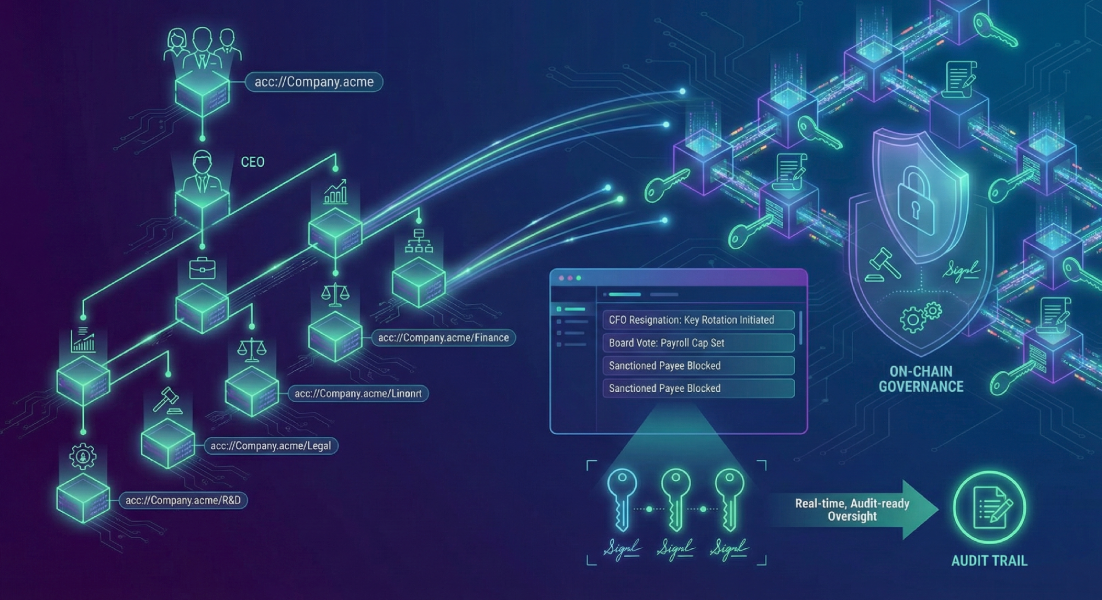
Inside Accumulate’s Hierarchical Key Architecture
Accumulate Digital Identifiers, or ADIs, resemble human-readable bank accounts—think treasury.bank—and must reference at least one Key Book for control; “each ADI must contain at least one Key Book,” notes the Accumulate whitepaper.
A Key Book is an ordered list of Key Pages. The first page wields upgrade powers over lower pages, mirroring how a board can replace department heads. Each Key Page sets its own m-of-n signature rule, baking multi-sig into the protocol instead of bolting it on through smart contracts.
Segregation of duties expands through Delegated Transactions. A payroll provider’s Key Book may co-sign only salary disbursements, while the treasury’s Key Book retains control of reserves. Because the signer list lives on-chain, any observer can verify that no outsider exceeded its remit.
Managed Transactions add a second, optional Manager Key Book that must approve high-risk transfers or those above a preset limit. The model echoes a two-man rule: operations staff propose, compliance officers release, and both signatures become immutable ledger entries.
Crucially, nothing in this stack depends on a separate policy server. Thresholds, role changes and spending caps are consensus facts, audited the same way as balances.
Use Cases That Unlock Institutional Demand
Treasury Operations. A controller initiates a payment, the CFO approves, and an observer key—sitting on its own zero-threshold Page—records the event in real time. The observer can never spend funds yet gives auditors continuous assurance, a workflow explored in an Accumulate blog on CeFi audit trails.
Payroll Sub-Accounts. Human-resources staff hold a Page capped at, say, 50 000 dollars per day. Breaching the ceiling automatically routes the transaction to the Manager Book. The treasury key never enters the workflow, so a leaked HR credential cannot drain reserves.
Qualified Custodian Integration. Under the SEC proposal, a registered investment adviser must house client crypto with a qualified custodian. Accumulate lets the adviser retain its Main Key Book while the custodian signs through a Manager Book, proving dual control on-chain without commingling wallets.
Tokenized Equity Settlement. In a 2022 prototype, Accumulate used Managed Transactions to enforce foreign-ownership limits automatically, showing how protocol-level governance can handle securities rules that change asset by asset Accumulate blog.
Compliance and Audit Edge
Traditional audits rely on snapshots: a firm attends a key ceremony, then issues a letter that expires the moment roles change. Key Books invert that model. Every threshold tweak, Page rotation or signer retirement is itself a ledger event, allowing auditors to test controls any day of the year.
Manager Key Books can even include an external auditor or regulator who co-signs withdrawals above a limit without ever touching operating keys. The arrangement matches the dual-authorization principle embedded in COSO while preserving confidentiality: auditors see hashes and signatures, not internal memos.
Because governance is native, downstream smart contracts inherit the same rules automatically. A DeFi lending desk, a tokenized bond and a rewards program all respect the same signer matrix, saving compliance teams from re-auditing every new application.
The result is continuous assurance, immutable evidence and reduced scope for both misconfiguration and insider fraud—advantages that off-chain MPC or contract-layer multisig cannot fully replicate.
Strategic Implications for Banks and Asset Managers
Analysts argue that stablecoins threaten fee pools across payments, deposits and credit. Yet many incumbents hesitate less because of regulation than because of custody risk. By embedding governance at the identity layer, Accumulate converts that weakness into a differentiator: institutions can offer 24-hour settlement without sacrificing their control environment.
A protocol-native model also future-proofs cross-chain strategy. Whether a bank issues its own deposit token, integrates an EU consortium coin or supports third-party stablecoins, the same Key Book can enforce policy across networks that recognize Accumulate identities.
That flexibility lowers switching costs, avoids vendor lock-in and positions governance—not raw transaction speed—as the true competitive moat in digital finance.
Conclusion
Crypto’s custody headache is not a hardware flaw. It is an architectural mismatch between single-key wallets and multi-party financial controls. Accumulate’s hierarchical Key Books close that gap by making governance an on-chain invariant rather than an after-market accessory.
As 24-hour money markets expand, the winning firms will be those that treat custody as code-level governance. With Key Books, losing a laptop no longer means losing the vault.
Sources
- Crypto.com. “The Institutional Stablecoin Nexus.” 08 Oct 2025.
- University College London. Exchange-governance research. 19 Jun 2025.
- Accumulate Whitepaper v1.0. 12 Apr 2022.
- PwC Switzerland. “Crypto Custody Risks and Controls.” 2023.
- U.S. SEC. Press Release 2022-219. 13 Dec 2022.
- U.S. SEC. Press Release 2023-30. 15 Feb 2023.
- Accumulate Blog. “Audit Trails for CeFi Creditors.” 22 Nov 2022.
- Accumulate Blog. “Tokenizing Public Equity Markets.” 13 Oct 2022.












Discussion